From SKID to SAVAGE by abusing OST and Telegram services.
In this post, I am going to show readers how easy it is for up-and-coming threat actors to completely compromise, then possibly extort large companies with very little effort by abusing openly available resources.

In this talk, I will be discussing the tools, tactics, and techniques used by threat actors in 2022 to gain access to sensitive information and compromise large companies.
In order to prevent this post from providing a step-by-step guide for aspiring blackhats in 2022/2023, I will not include any details on how to maintain operational security and avoid detection while using the techniques I am discussing.
Prerequisites
To make sure everyone is on the same page, I am going to set a few general definitions here in case you are new to the threat-intelligence world, since these terms may be referred to later in the post.
- Database Broker - A database broker is an individual or group that specializes in buying and selling access to databases that have been obtained through illegal means, such as hacking.
- Access Broker - A access broker is an individual or group that specializes in buying and selling access to computer systems, networks, and data.
- Stealer Service - A stealer service typically involves the sale of software or access to software that is designed to steal sensitive information, such as login credentials or financial data, from individuals or organizations.
- Botnet Vendor - A botnet vendor is an individual or group that sells access to botnets on darknet markets. A botnet is a network of compromised computers that are under the control of a single entity, often without the knowledge or consent of the computers' owners.
You can see by the definitions above, the markets have been created due to demand, and each market can contribute to the others to maintain a strong eco-system. For instance, if someone builds some new Stealer malware and wants to start a Stealer Service, they could pay the Botnet Vendor to deploy their stealer to N number of machines. Once information is stolen, the Stealer Service can sell off valid logins found in the stealer logs to Access Brokers. The Access Brokers may have access to backend services such as databases, which will be exfiltrated and sold to Database Brokers. See how this is a cyclical operation?
With that out of the way, let's get a little background into the process.
Background
If you have been following the news lately, you may have heard about the recent hacks of Uber and Rockstar, in which a hacker managed to infiltrate each company's internal network, steal and leak sensitive development and production code, and other data to the public.
Many people in the threat intelligence industry were already aware of the likely culprits behind the attacks before any official announcements were made by Uber or Rockstar's PR teams. Furthermore, those of us who had participated in Uber's HackerOne Bug Bounty program had a good understanding of the company's network infrastructure and potential vulnerabilities, so it was surprising to us how a hacker was able to gain such extensive access to a supposedly well-secured network.
About a week after the attack, Uber released the following on their Newsroom page.
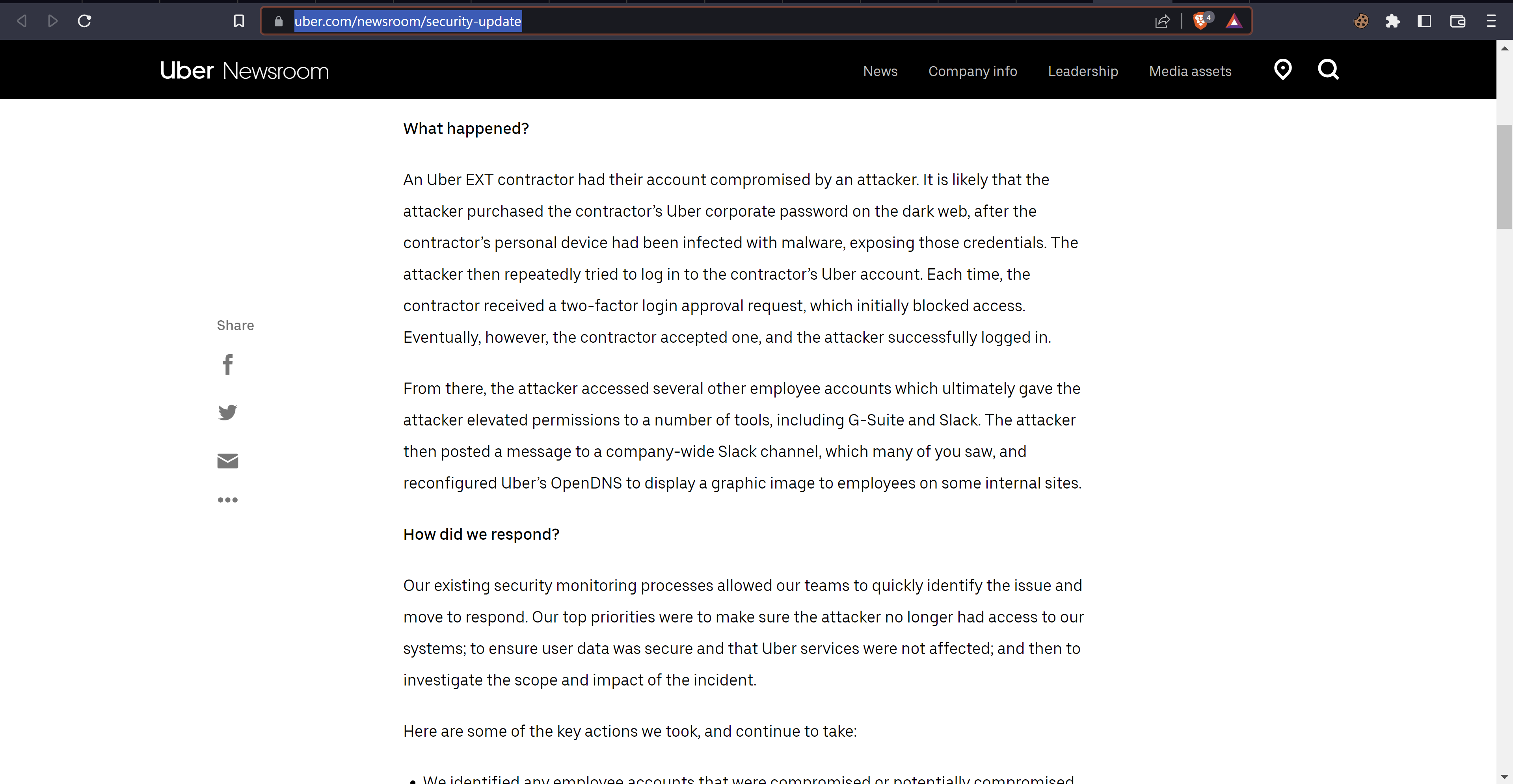
This confirmed the suspicion for many of us in the community, that the hacker didn't find a bug in Uber's network per se, but was able to obtain access to the network via stolen credentials which were sold on the dark web.
Upon learning this, many people in the threat intelligence community immediately suspected that the Lapsus$ group was behind them, and they turned out to be correct.
Lapsus$ is a group of hackers who began carrying out high-profile cyberattacks in late 2021. They initially focused on South American companies, but eventually expanded their targets to include high-profile companies.
The first significant cyberattack attributed to Lapsus$ occurred against the Brazilian Health Ministry's computer systems in December 2021. In March 2022, the group gained notoriety for a series of attacks against major tech companies, including Microsoft, Nvidia, and Samsung. Following these attacks, the City of London Police arrested seven individuals in connection with an investigation into Lapsus$. Although the group was believed to be inactive by April 2022, they reportedly resumed their activities in September 2022 with new data breaches against various companies, including Uber and Rockstar Games. The City of London Police made additional arrests in connection with these attacks.
One of the former members of Lapsus$, known by the aliases sigmA, wh1te, teapot, etc., was arrested and charged with two counts of "breach of bail conditions" and two counts of "computer misuse." The individual pleaded guilty to the first two charges, which were related to previous arrests in connection with the Lapsus$ group. The individual pleaded not guilty to the second two charges, which were related to the recent hacks.
The hacker wh1te was already known to authorities due to his personal information being posted on d0xbin, a website that he briefly owned before it was sold back to its original owners at a greatly reduced price, as mentioned in the below d0xbin post.
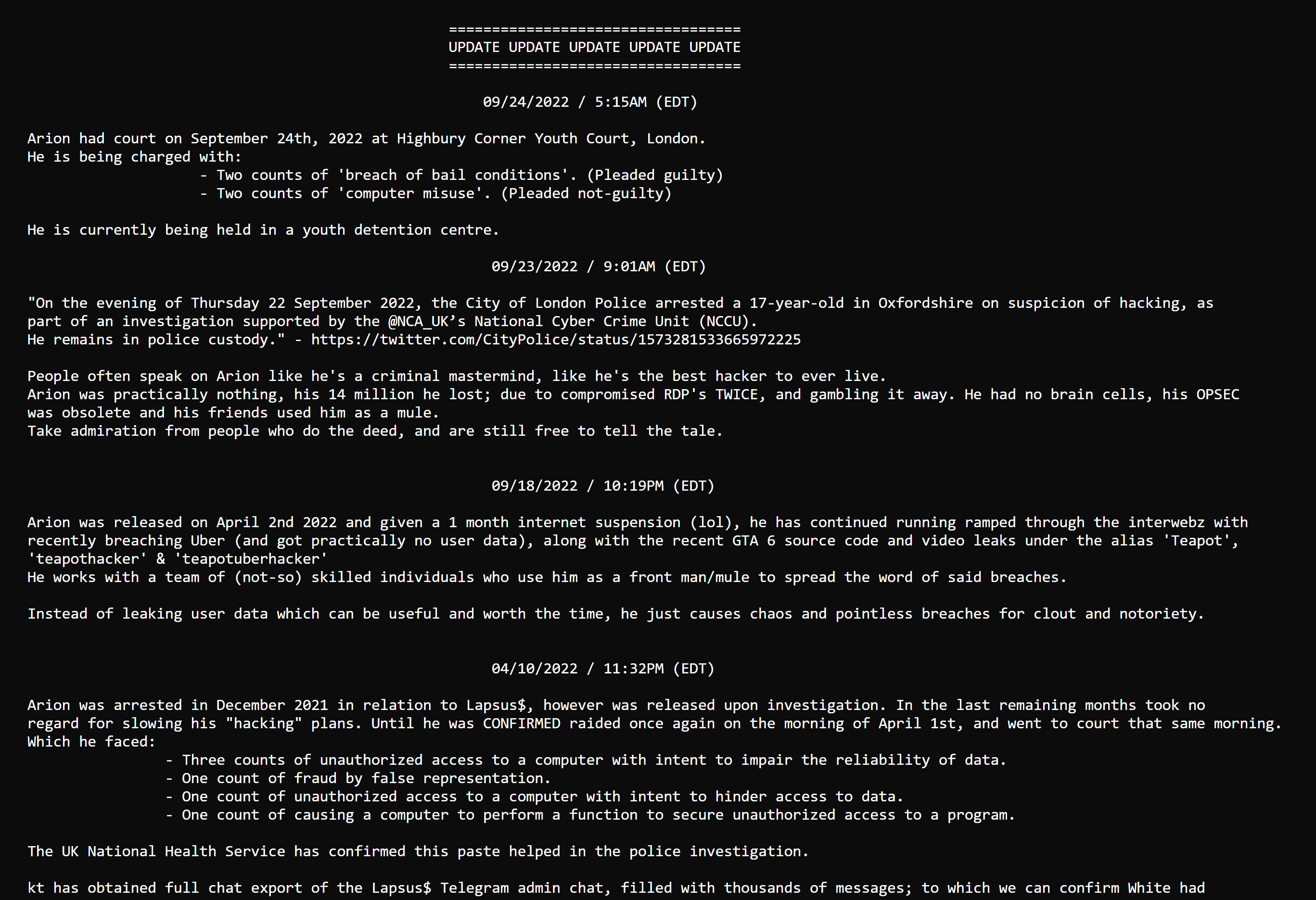
Now, how was this 17-year-old able to hack into such well-secured networks? I will demonstrate one possible method that these hackers may be using to achieve similar results.
Let's examine a hypothetical scenario in which a threat actor replicates similar actions of the Lapsus$ gang during an Uber-like attack and illustrates how easy it is to carry out such an attack.
Scenario
In this scenario, the hacker is given the task of infiltrating the internal network of a large company with the goal of extorting them, using ransomware, or exfiltrating sensitive data as quickly as possible.
Step 1 - Setup new identity:
In this scenario, the first step would be for the hacker to create a new email and identity for this operation. To do this, they will use the elude network to set up an email and gain access to some crypto wallets.
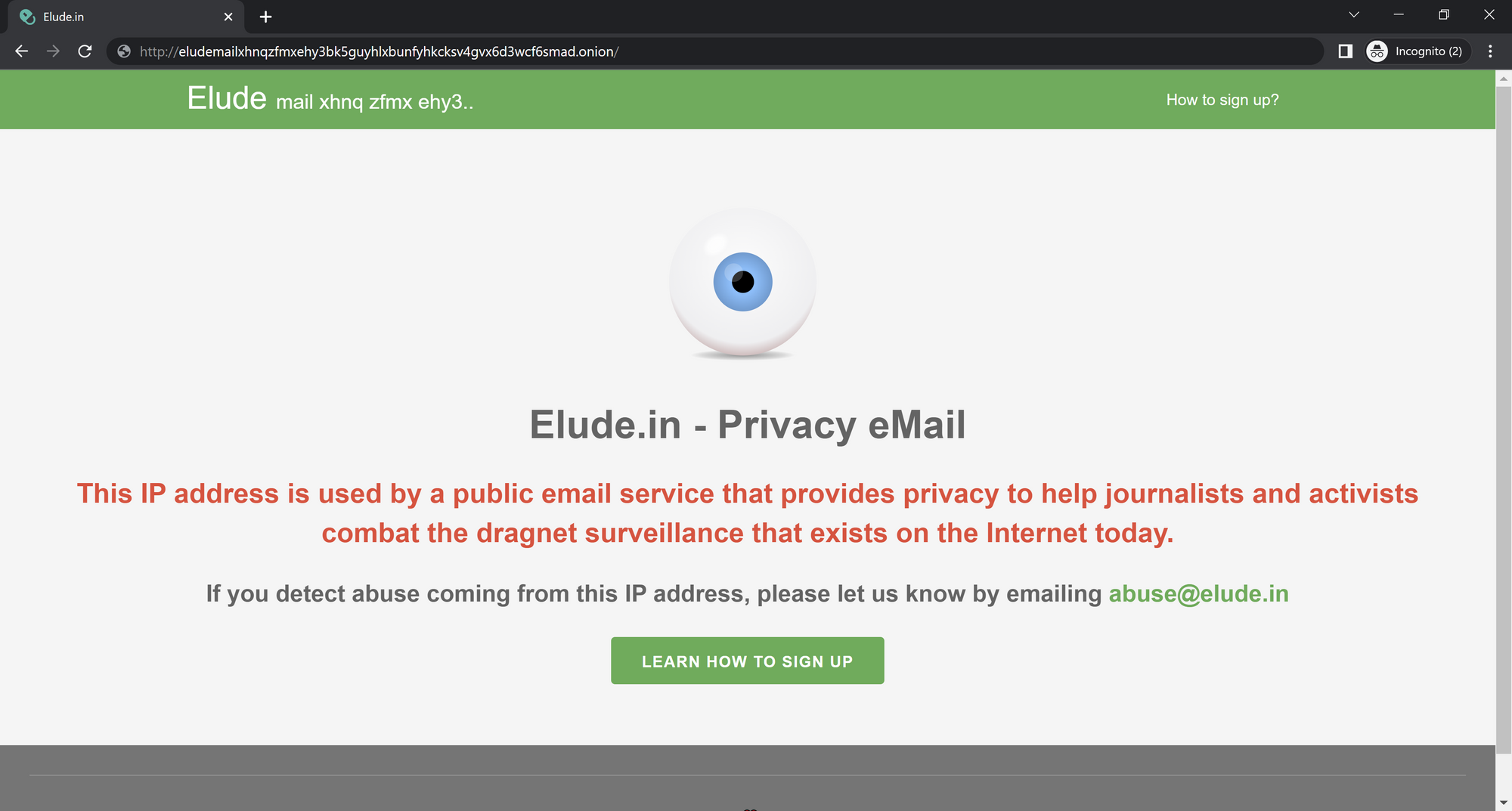
By adding a small amount of BTC, LTC, or XRP to your wallets, you will gain access to email hosting on the elude network. This email address will allow the hacker to start creating an identity on the forums.
Step 2 - Setup forum accounts:
After creating a new email, the hacker will then use it to set up accounts on various hacker forums, such as Breached, as seen in the image below.
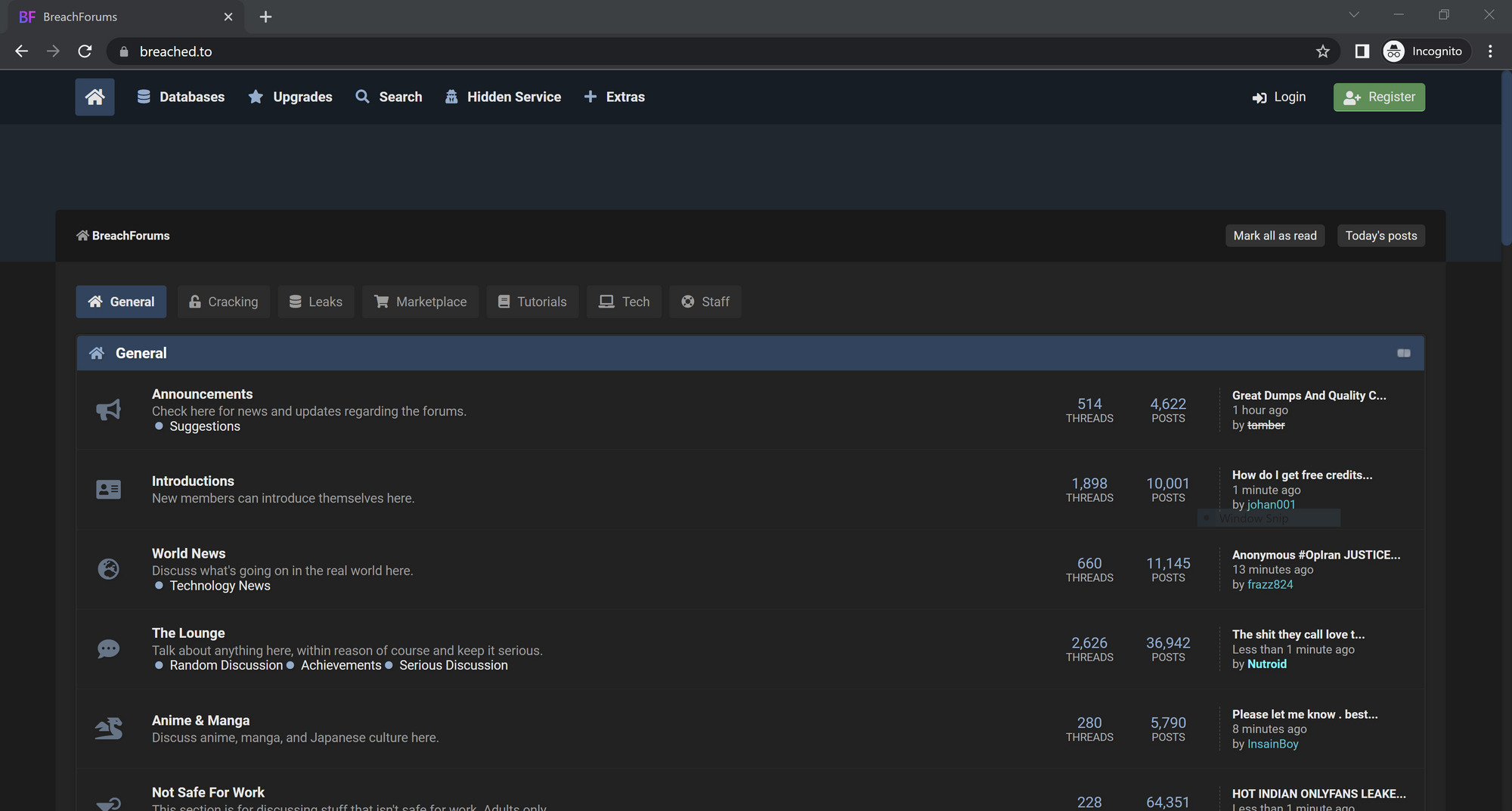
With access to hacker forums, the hacker can now learn about the current state of the darknet marketplace. From there, they can easily locate and contact access brokers who may be able to provide the necessary tools and information for their attack.
In this scenario, the hacker is a newcomer to the forum and knows that it is unwise to immediately approach access brokers to purchase access to systems. In order to complete their task, they will need to try another method.
In order to establish some leverage, the hacker asks database brokers what targets are in high demand at the moment. They mentioned that databases from the Russian government containing login credentials are valuable, as the country is currently at war with a neighboring nation.
Looks like the hacker needs to get to work.
Step 3 - Abusing OST:
Knowing the access brokers are looking for databases containing login credentials for a specific government, the hacker will need to start doing some actual hacking in order to achieve their primary goal. They know the quickest way to obtain such a database would be to find a SQL Injection bug that the hacker could quickly exploit to exfiltrate the database from a vulnerable server.
The hacker begins researching all known government domains associated with the target country. They know that gov.ru is the main root used for Russian government domains, so they quickly gather as many domains containing gov.ru as possible in order to maximize their chances of success.
There are many resources and tools for sub/domain enumeration, but for the sake of this scenario, the hacker used the site crt.sh to pull all the gov.ru domains in its database as seen below.
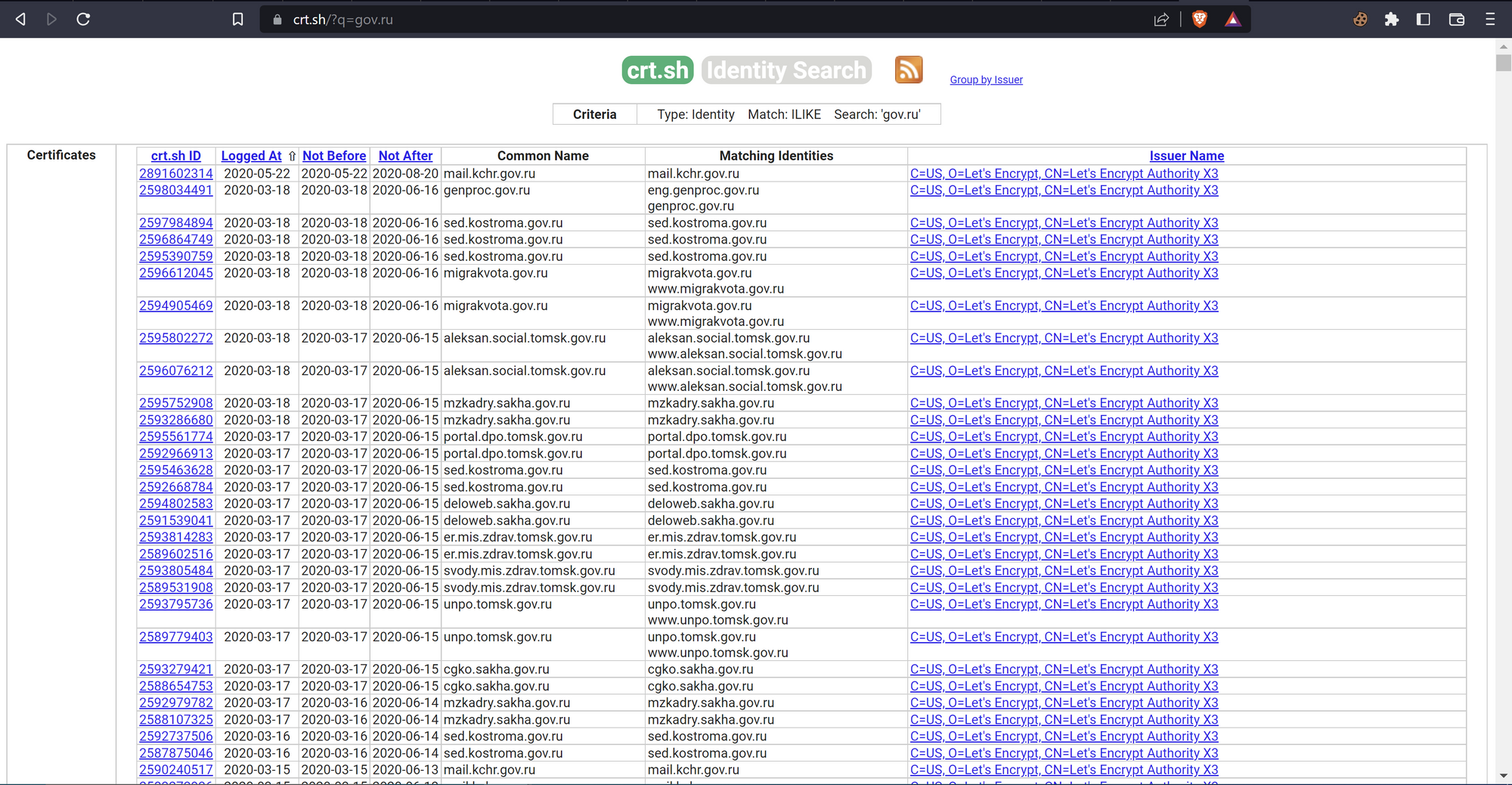
The hacker then uses a grep command to extract all gov.ru domains and puts them in a separate file for further processing. Once done, the hacker will use the following methodology to find a SQL Injection.
- They run tools like
amass,subfinder, andchaoson the discovered domains to obtain a list of subdomains associated with eachgov.rudomain. - Once the tools have finished running, the hacker uses
httpxto check for the top 1000 web ports across all domains to identify which ones have running web services. - They then use
katanato crawl each domain and enumerate all its endpoints. - With a list of all the discovered endpoints, the hacker runs
getdirsto extract all the possible directory paths. - They then use
nucleiwith the tagssqlioption, using the output fromgetdirsas input, to check for SQL injection vulnerabilities at each directory level. - Finally, the hacker runs
sqlmapagainst some of the possible injections discovered bynuclei.
After about 24 hours, the hacker not only discovers several potential SQL injection vulnerabilities but also successfully exploits one and extracts a large database containing over 50,000 users with login information. This is exactly what the database brokers are looking for, so the hacker returns to the forums to barter.
Step 4 - Abusing Telegram:
Since the hacker is not interested in money or reputation, and their initial goal was to gain access to a large company for malicious purposes, they offer to trade the database for information or an introduction to a premium Stealer service. The database broker is happy to receive the database for free and provides the hacker with a few names of colleagues on Telegram to contact. The hacker is instructed to let them know that they were sent by the database broker or their gang, and that this would get the hacker access to 1 week of a premium stealer service.
Upon joining the private Telegram channel, it was evident from the listed prices that the database broker valued the database at around $300 USD, as that was the going price for one week of premium stealer logs to a group of approximately 10 people.
It was also clear that the Stealer service administrator had chosen Redline Stealer as their stealer of choice, which is a common choice in the Stealer markets at the moment. The administrator was also willing to accommodate users in the channel who requested logs from specific countries or regions, allowing them to narrow down their target landscape.
Every hour or so a new dump of logs would hit the channel in .rar format, which was quickly downloaded and parsed by all the hackers in the channel, however, the logs were so big, there is no way a group of 10 could properly parse these files within an hour. It was clear a lot of the hackers were going after crypto wallets and had their own private tools for quickly cracking and dumping wallets of all different types, but this hacker's goal wasn't to earn money, it was to gain access to a large company's internal network.
Step 5 - Achieve goal:
After a few hours of dumping and parsing all the Passwords.txt files contained in the stealer logs, a few interesting logs starting to pop up.
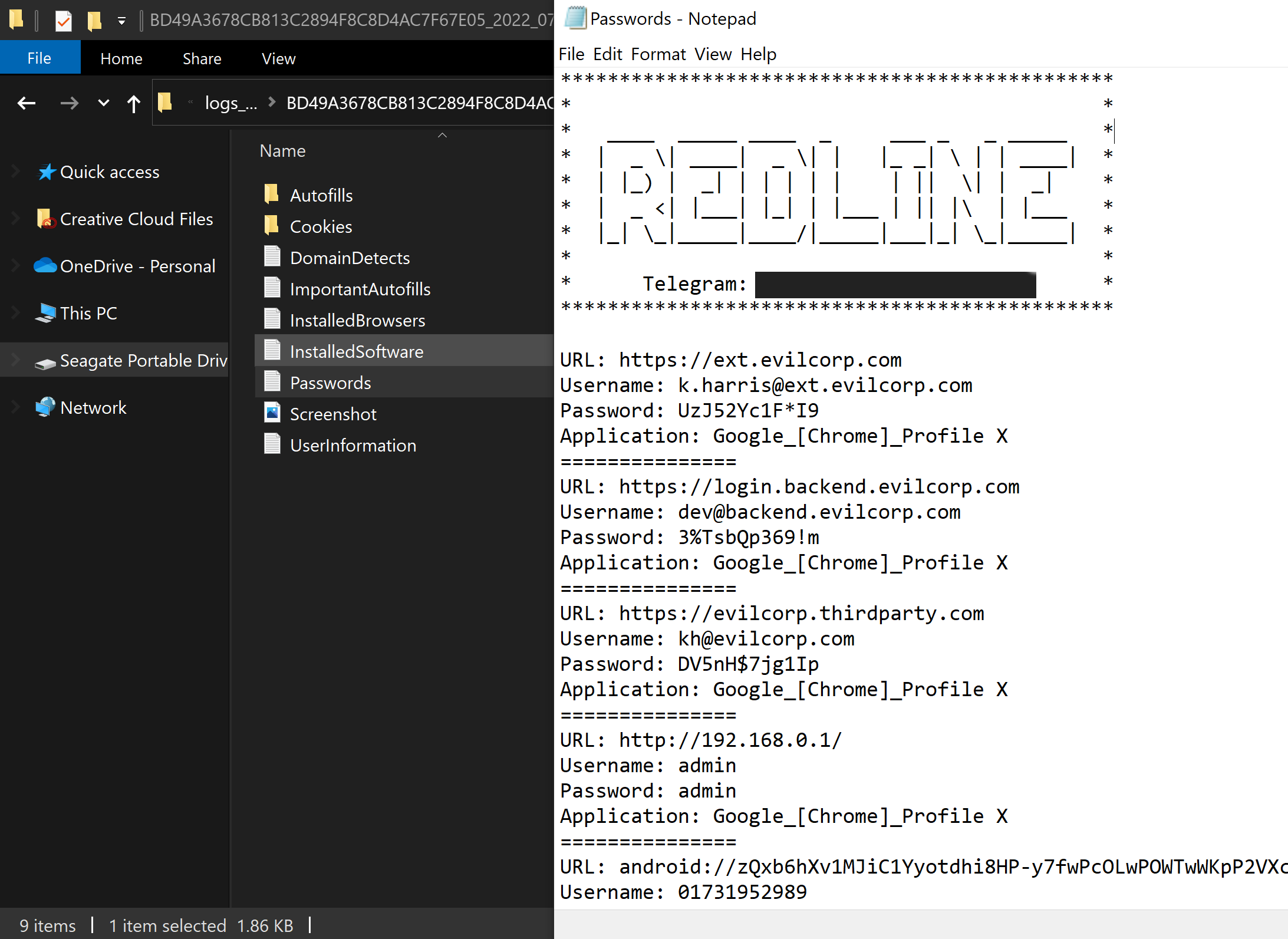
The following accounts stood out when parsing the latest log dumps.
k.harris@ext.evilcorp.com
dev-01@backend.evilcorp.com
kh@evilcorp.com
It seems a person working at Evil Corporation named Kim Harris was infected by stealer malware and had their browser credentials stolen, including a external login, developers portal login and a third-party authentication service.
The logs for this user also contained the geo-location and IP address used when connecting to some of the endpoints. By using residential proxies that were located very close to the target, the hacker was able to gain access to one of the three credentials listed above, which provided access to the development portal of a branch of Evil Corp.
This was a good login, but wasn't connected to the internal network. However, the credentials for kh@evilcorp.com were correct, but wanted to send a push notification to the user before we would be able to sign in. Using a little trick, the hacker would call the user and hang up while sending the push notification at the same time. After doing this about 5 times in a row, Kim Harris pressed the 'Accept' option which allowed the hacker into the third-party authentication service, and bingo... this is exactly what the hacker wanted.
Now that the hacker has obtained valid credentials, used a residential proxy close to the victims geo-location to attempt a login, then was able to trick the Evil Corp. employee into clicking "Accept" to a login push notification by spamming requests, it is time to start parsing through all the data within the authenticated environments much like wh1te did with the Uber hack. After finding some good information, the hacker starts to exfiltrate all the data that looks sensitive, confidential or under development such as source code back to their own machine.
Once the hacker has everything they want from the internal servers, it is literally up to them what to do next. It seems taking screenshots and flexing on Twitter isn't something this hacker was going to do.
The hacker, being successful at their task, will report back to their over lords about their success and call it a day.
Conclusion
Although the scenario may seem straightforward, I can assure you that it is indeed real. This was simply a brief glimpse into the world of darknet markets, and a potential scenario in which a new threat actor could achieve "breaking news" results in just a few days.
The ease at which any hacker worth a shit could pull this attack off, should fucking scare you. With better loaders and malware to bypass most AV/EDR detections, even YOU are one 0day bug away from being added to the Stealers victim list.
It should also be shocking that these Stealer Vendors on Telegram as mentioned in the scenario, are EASILY accessible on public channels as well. All you have to do is search for "Redline" or "Eternity" and you will find vendors ready to sell you logs. Some groups on Telegram will actually dump fresh stealer logs for free just to get people started.
If you would like to know more about my research or about darknet markets, please shoot me an email at d3d@malicious.group, since my Twitter account was suspended.




Comments ()